What Is Cryptolocker? How To Fix and Decrypt Cryptolocker Ransomware
What is Cryptolocker?
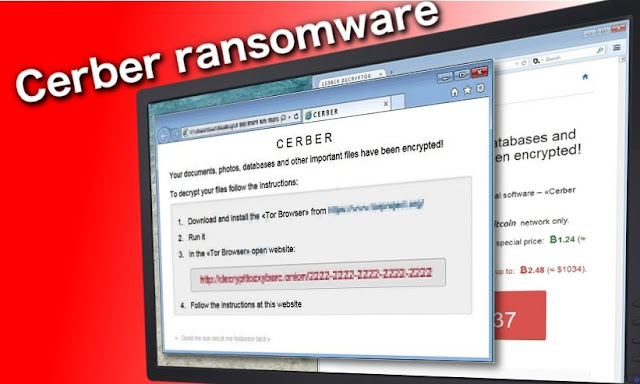
CryptoLocker infection is a ransomware infection which was at first seen in 2013. A year after, the gathering of infection scientists figured out how to control this infection by closing down its primary merchant — the Gameover Zeus ransomware. From that point forward, the first undertaking was however to be dead, yet different CryptoLocker renditions have been rising.Despite the fact that the a large portion of new Cryptolocker variations were composed by beginner programmers, some of variations have surfaced the web and truly got specialists thinking whether this ransomware isn't raising from the dead. Unfortunately, the most recent its variant, called Crypt0L0cker, has made heaps of harm PC clients.
All in all, might it be able to be that the web group's most exceedingly terrible bad dream is turning into a reality in 2017? Contemplations that Cryptolocker is coming back to recover its the most unsafe ransomware put have been activated by the way that digital hoodlums who are in charge of discharging it may be out of their 3 million dollar benefit.
In the event that you believe that you could be tainted with this infection, don't dither to evacuate CryptoLocker. This is the most straightforward approach to end its movement on the framework. In the event that you let this malware remain on your PC, this ransomware can cause much more harm by scrambling another segment of your documents.
How does this infection work?
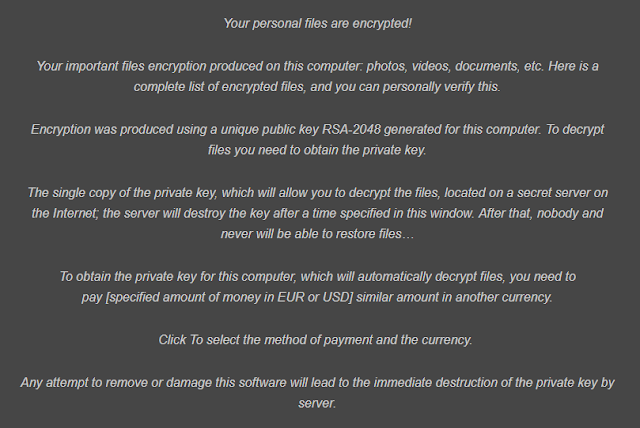
The principle objective of Cryptolocker is to invade your PC without your insight. For that, malware depends on apparently innocuous email messages. These messages regularly contain vindictive connections which convey the payload of the ransomware. Once the casualty is deceived into opening it, the infection invades the objective PC framework, scrambles casualty's documents and shows a payment note which is shown beneath.Regardless of that it has a place with an indistinguishable class from FBI infection, Police Central e-wrongdoing Unit infection or Department of Justice infection, this infection tries to persuade its casualties that they need to pay a payoff by scrambling their own documents. CryptoLocker is the document scrambling ransomware, so it utilizes RSA open key cryptography to bolt the accompanying record sorts on casualty's PC:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx.
As should be obvious, this rundown is brimming with generally utilized records names, for example, doc, xls and comparative. To reestablish them, Cryptolocker ransomware requests that you pay a payment through Moneypak, Ukash, cashU, or Bitcoin. Regularly, this danger asks from $100 to $500, however the cost can be expanded at any point in the near future.
As indicated by the notice message, which is normally shown by this risk, individuals have just a specific measure of time to pay a payoff and recoup the association with their documents. Cryptolocker leaves the alleged payment note, which grandstands such data:
Luckily, Cryptolocker can not hurt the individuals who have been moving down their information and making additional duplicates of their documents. In the event that you have duplicates of your photographs, business reports, and different records, you don't have to pay a payoff. You simply need to expel this ransomware from your PC and keep the extra harm.
Also Read : https://www.howtoremoveit.info/free-antimalware-software/
For Cryptolocker evacuation, we exceptionally prescribe utilizing Reimage, which has been demonstrating extraordinary outcomes while wiping out records of this infection. For reestablishing your records, we sympathetically request that you read information recuperation alternatives gave underneath the article.
In any case, it appears that fakes have chosen to facilitate the standards for casualties who pay the payment however basically can't accumulate the settled measure of cash inside the predefined measure of time. Regularly, when the counter infection programming erases the ransomware, the casualty can never again pay the payment.
In this manner, the most recent adaptations of CryptoLocker have another element to change the desktop's backdrop when the counter infection identifies the danger and show a message on the screen advising the casualty where to download the ransomware again in the event that he or despite everything she needs to purchase the unscrambling programming.
In spite of the fact that we exceedingly suggest not paying the payment, we comprehend that a few organizations won't not have the capacity to get by without individual information that has been put away on the traded off PCs, so in such cases, paying the payment may be the main opportunity to develop the business. Once more, we advise you that we don't suggest paying up. Remember that you can never make sure whether lawbreakers give working decoding instruments!
Strategies used to remove cryptolocker ransomware
CryptoLocker is considered as a standout amongst the most proficiently conveyed crypto-ransomware infections and, talking about its appropriation, we need to state that writers of this infection consolidate a few distinct systems to spread the virus. It has been seen that they utilize both old and new dissemination procedures, neglecting to agree to any ethical standards.As per specialists, Cryptolocker infection is spread utilizing authoritatively looking messages, counterfeit pop-ups, and comparative strategies. Prior, ransomware has been disseminated through ugly email letters that contained malevolent connections, malware-loaded promotions, which publicize projects or updates that really contain the infection official record, or endeavor units, which enabled hooligans to contaminate casualties' PCs by misusing their PCs' vulnerabilities.
Be careful that this risk can penetrate your PC through phony fly up that claims that you have to refresh your Java, Flash Player or comparative program, so ensure you introduce these projects from their checked designers' destinations, not from some suspicious outsider locales.
On September 2016, a few new ransomware appropriation systems have been spotted. The first depends on vindictive messages acting like letters from power provider VERBUND. This organization isn't identified with these con artists in any capacity – they simply utilize a trustworthy organization's name to persuade clients to tap on noxious connections or open irresistible email connections containing CryptoLocker ransomware.
The message subject is Detailaufstellung zu Rechnung. In the event that you have gotten such letter, erase it quickly without tapping on joins incorporated into the message or opening connections it contains!
The second ransomware circulation technique that has been found is a grimy and revolting approach to trap the client and power him or her to open the malevolent record containing the infection. Tricksters act like representatives of human services organizations and send beguiling messages that can cause a heart assault for the casualty. They convey a false blood test report, expressing that the casualty may experience the ill effects of tumor because of the absence of white platelets.
The message makes a request to print out the blood test comes about that are in a joined report and convey these to the family specialist ASAP. Such news can influence anybody to frenzy, and power to open the appended record without suspecting this is only a goad. At the point when the hopeless casualty opens the connection, the ransomware takes control over the framework and encodes every one of casualty's records with no regret. As should be obvious, digital culprits can go low since all they think about is cash.
Tips on the most proficient method to shield your information from being encoded
On the off chance that you need to remain safe, you ought to never trust deceiving advertisements that put on a show to be useful in light of the fact that the main thing what they do is spread infections and futile projects. Likewise, ensure you erase spam and twofold check each email that was sent to you by obscure senders. In addition, keep in mind to incapacitate shrouded augmentations (on the off chance that you are utilizing Windows OS) and, to stay away from the loss of your documents, you should consider their assurance.You can also read : https://www.howtoremoveit.info/adware-what-is-adware-virus-remover-and-adware-removal-tool/
The primary thing that you ought to do is to download a respectable hostile to spyware on your PC. We suggest utilizing Reimage. Also, ensure you perform reinforcements as much of the time as conceivable in light of the fact that this could help you to recoup your scrambled documents. At long last, you should utilize such arrangements as Google Drive, Dropbox, Flickr, and so on when attempting to ensure your critical records. Be that as it may, remember this effective infection may have the capacity to get to these online stockpiling places by means of your Internet association and scramble these documents, as well.
Consequently, it is prescribed putting away information reinforcements on removable capacity gadgets, for example, hard drives or USBs. Tragically, in the event that you are contaminated with this ransomware at this moment, you should realize that there is no official Cryptolocker ransomware decode device yet. In any case, you can check the guide given on the second page of this post and recuperate your records with some extraordinary instruments. Bear in mind to evacuate ransomware before recuperating your documents since it might cripple them once more!
Also Read : http://anti-malware-software.webnode.in/l/what-is-cryptolocker-how-to-fix-and-decrypt-cryptolocker-ransomware/



Comments
Post a Comment