Cerber Ransomware - How To Remove Cerber Ransomware Virus From Your Computer.
What Is Cerber Ransomware?
A standout amongst the most dynamic sorts of ransomware out
there, Cerber encodes the records of contaminated clients and requests cash in
return for offering access to their documents back. It works regardless of the
possibility that you are not associated with the web, so you can't stop it by
unplugging your PC.
Ordinarily, the casualty gets an email with a contaminated
Microsoft Office report joined. Once opened, the malware scrambles documents
with RC4 and RSA calculations and renames them with a .cerber augmentation (if
contaminated with one of the prior variations of the malware) or an arbitrary
record expansion in the most recent forms.
Who is Cerber ransomware focusing on?
Everybody and anybody — aside from clients in specific
nations. In the event that the malware identifies your PC is from Armenia,
Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia,
Turkmenistan, Tajikistan, Ukraine or Uzbekistan, it will deactivate itself — in
any event for the time being. Try not to accept you're protected in case you're
situated in any of these nations. Things can change, and they frequently do.
Where does Cerber originate from?
From Russia, possibly. It positively flourishes in Russian
discussions in the profundities of the dim web, where it can be purchased and
conveyed for around 40 percent cut of the payment benefits, payable to the
designers. Likewise, the way that it declines to assault previous Soviet
nations is a bit gee.
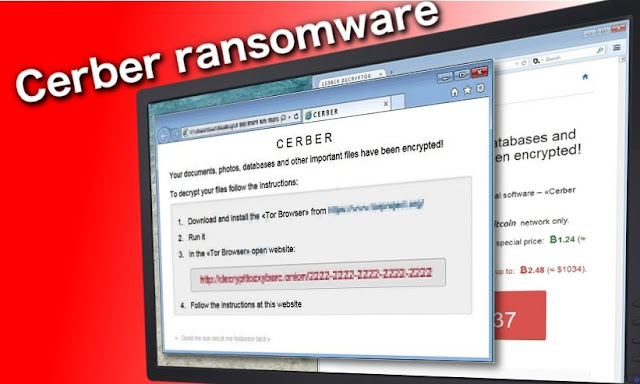
The most effective method to perceive Cerber ransomware
Your first intimation that your PC has been tainted with
Cerber will come after you sign in, in light of the fact that your desktop
backdrop will have been changed to show a desktop note.
You will likewise observe three payoff notes left on your
desktop and inside any organizer that the malware has scrambled. These notes contain
directions on the most proficient method to send the payment installment to the
aggressors — a sum that seems to increment with time. Contingent upon the
bitcoin swapping scale, this payoff installment extends from a few hundreds to
over a thousand US dollars.
Additionally, it talks. One of the payment note Cerber
abandons is a .vbs document that influences your PC to hand-off an electronic
voice message rehashing that your records have been encoded.
Instructions to remove Cerber ransomware
Avast antivirus innovation recognizes and evacuates Cerber
ransomware, and additionally different sorts of malware. On the off chance that
your PC is contaminated with Cerber ransomware, our antivirus will recognize
it, isolate it and annihilate it. In the event that it identifies Cerber is
attempting to enter your PC, it will piece it from getting in.
Lamentably, there is no Cerber decryptor that attempts to
recuperate documents that have just been scrambled. This is the reason
counteractive action is basic.
Step by step instructions to Remove Cerber ransomware Virus
Cerber's encryption is unbreakable, so once your records are
encoded, there is nothing you can do to get them back. Notwithstanding
submitting to the aggressors' criminal requests for installment would not
ensure that your records will be unscrambled, as there is nothing keeping them
from simply taking your cash and running. Your most logical option, along these
lines, is to prevent Cerber from getting into your PC in any case.
Having a breakthrough antivirus introduced in your PC is
your first line of guard. Great online wellbeing practices can go far in
keeping you and your information secure —, for example, failing to open
suspicious email connections, regardless of the possibility that you know and
put stock in the sender. In the event that it looks or feels off, don't chance
it.
Cerber is only one of the many strands of ransomware out
there, and ransomware itself is just a single of numerous sorts of malware that
can hurt your PC, your information and your security on the web. On the off
chance that you are searching for an exhaustive and thorough malware expulsion
and avoidance apparatus, Avast has got you secured — from the basic insurance
of our Free Antivirus, to the propelled security and execution highlights of
How To Remove It.
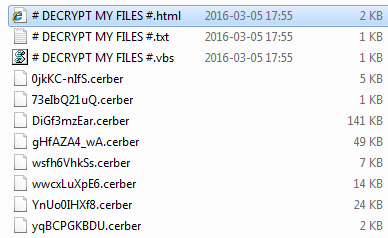
Cerber Ransomware is a Malicious document scrambling infection that
locks clients record utilizing solid encryption algorithm. Malware has been
refreshed a few times and right now can annex .cerber, .cerber2, .cerber3,
.af47, .a48f, .[random characters] document augmentations to each of the
focused on records. When it's set, malware drops a payment note where
casualties are advised to pay the payoff with a specific end goal to get back
their records.
The ransomware changed the name of the payoff take note of a
few times – diverse renditions of this crypto-malware were spotted utilizing
such names for the payment notes: # DECRYPT MY FILES #.txt, # DECRYPT MY FILES
#.html, # HELP DECRYPT#.html, _READ_THIS_FILE.hta, *HELP_HELP_HELP[random
characters]*.hta, _R_E_A_D___T_H_I_S___[random]_.txt or
_R_E_A_D___T_H_I_S___[random]_.hta.
Like some other document encoding infection, a client may
experience it by means of malevolent spam messages that convey a tricky .ZIP,
.DOCM, .PDF, or .JS record. An intriguing insight about Cerber ransomware is
that it won't assault your PC in the event that you live in one of these
nations – Azerbaijan, Armenia, Georgia, Belarus, Kyrgyzstan, Kazakhstan,
Moldova, Turkmenistan, Tajikistan, Russia, Uzbekistan, Ukraine. On July,
specialists additionally saw a gigantic malvertising effort assaulting
individuals in South Korea. Sadly, if none of these is your nation of current
living arrangement, this infection may possibly hit your PC.
It sets itself to run naturally on the following PC startup.
Once the PC winds up noticeably dynamic, ransomware begins sending arbitrary
mistake messages and after that reboots your PC into Safe Mode with Networking.
Tragically, the infection at that point restarts your PC once more, this time
in a typical administration, and begins the encryption procedure. The most
recent its rendition has gotten an immense refresh – now it utilizes red
shading for the payment note used to caution the casualty about the scrambled
information.
Once the encryption procedure is done, Cerber ransomware virus drops recover notes in every organizer that stores tainted records. These notes
are named as DECRYPT MY FILES. The document augmentation may fluctuate, it can
be a .html, .txt, or .vbs record. The .vbs record will likewise play a sound
message, which says:
Consideration. Consideration. Consideration. Your archives,
photographs, databases and other essential records have been scrambled!
The payoff note discloses what happened to your PC and gives
directions how to recover your records. Without further ado stated, infection
engineers request that you download Tor browser to get to the site where you
can pay the payment namelessly. It requests the casualty to pay 1.25 BitCoins,
which is roughly $512 USD. It additionally undermines that the payment will be
multiplied if the casualty does not pay inside seven days. In the event that
the payment is paid, this ransomware ought to as far as anyone knows give a one
of a kind download connect to get a method to decrypt cerber ransomware. Something else,
there is no real way to unscramble petitions for nothing.
Refresh July 2017: Security specialists report that Cerber
continues growing and searching for new adaptation strategies. As of late, an
enormous assault hit South Korea. Other Asian nations have additionally
experienced the ransomware. Scientists take note of that offenders have been
spreading malware in this district for a couple of months with the assistance
of Magnitude misuse pack.
Ransomware spread with the assistance of malvertising. At
the point when a client visits a vindictive site, the malware checks few
insights about the clients with a specific end goal to choose – to dispatch the
assault or not. These "entryways" are known as "Magnigate"
and check client's IP address, ISP, and the data about working framework and
web program. Along these lines, Cerber infection can dispatch focused on
assaults and abstain from penetrating arbitrary PCs.
To support their earnings, designers of the Cerber
ransomware made another variation that is equipped for taking Bitcoin wallet
data. After the penetration, it takes passwords put away in the Internet
Explorer, Google Chrome, and Mozilla Firefox web programs. When it's set, it
ends up noticeably less demanding to acquire data from Bitcoin wallets.
Checkout Our latest blog on : Chinese Gender Predictor
The infection searches up with the expectation of
complimentary records that have a place with the diverse Bitcoin wallet
applications:
wallet.dat utilized by Bitcoin Core wallet;
*.wallet utilized by Multibit wallet application;
electrum.dat utilized by Electrum wallet application.
Another verification that Cerber keeps developing and
growing is a current coordinated effort with engineers of Kovter Trojan. This
digital disease is referred to since 2013 as snap misrepresentation malware.
Both malignant projects were seen spreading with spam messages that conveyed
counterfeit warnings from distribute administrations, for example, FedEx, USPS,
and UPS.
In this manner, once casualties are deceived into opening a
muddled document, they download two rather than one digital contamination.
Therefore, casualties can get their records scrambled as well as lose
individual data, for example, login points of interest.
Refresh June 2017: Cerber malware rises again and utilizes
an alternate payment take note of this time. The infection encodes considerably
more documents and drops a payment note called
_R_E_A_D___T_H_I_S___[random]_.txt or _R_E_A_D___T_H_I_S___[random]_.hta. The
payment note begins with an unexpected line in comparison to whatever remains
of Cerber deliver notes – it says "Howdy, I'am CERBER RANSOMWARE 😉."
The infection requests a large portion of a Bitcoin (around $1195) and builds
this cost to 1 BTC in 5 days.
The ransomware is still effectively advanced through Blank
Slate spam battle that conveys a huge number of messages to casualties. These
messages convey a ZIP in a ZIP record, and once these two documents get
removed, a [random digits].js document gets dropped on the framework. On the
off chance that the casualty opens it, the content within it interfaces with a
remote server and downloads ransomware from it.
Refresh April 2017: In April 2017, analysts recognized new
transformations in the dissemination of this infection. This time, individuals
behind Cerber venture focused on vulnerabilities in Apache Struts 2 on Windows
servers. In any case, Apache Struts is a free and open-source structure for
making Java web applications. For reasons unknown malware merchants have been
assaulting frameworks running projects made with Apache Struts and setting up
secondary passages, selecting gadgets into DDoS bot arrange, putting digital
money mineworkers and obviously, pernicious infections like payoff
The weakness in Apache Struts programming enabled crooks to
target servers rather than singular PCs, furnishing them with opportunities to
achieve potential casualties that definitely have cash and probably will pay up
just to gain the power of the information back.
The aggressors utilized an endeavor code that enabled them
to run shell charges and dispatch BITSAdmin utility, lastly download Cerber
ransomware from a remote server. Presently, specialists have found that this
specific bit of ransomware adjusts Windows Firewall manages and keeps
correspondence from introduced antivirus to the world, making it difficult to
introduce antivirus updates or sending reports to the designer. As indicated by
specialists, the Bitcoin wallet address utilized by this form of the notorious
ransomware continues as before.
While the dialog about Cerber has secured, clients may have
let their protect down persuaded that the malware has blurred into obscurity.
Such intuition may be hazardous, as the programmers are yet to strike once
more. As of late pros have identified this hazard covered up in Dropbox
documents. While on account of normal spam messages, a client still needs to
separate the connection all together for to initiate the disease.
The engineers found a workaround to this component and
spread this crypto-malware by means of self-removing Dropbox records.
Fortunately, regardless they should be "clicked" keeping in mind the
end goal to dispense harm. There is another influx of this malware coming:
TrendMicro infection report uncovers different new forms of the risk:
Ransom_Cerber.R000C0DD517, Ransom_Zerber.R08NH0CD317, and so on. The report
additionally uncovers that the most recent rendition is likewise ready to
maintain a strategic distance from machine learning location by security
applications. Ceaseless re-stacking of the executable documents counteracts
discovery. In any case, authorities console that multilayer security
programming is as yet a legitimate arrangement when managing Cerber.
Refresh February 2017: In the start of February, security
specialists saw another variant of Cerber ransomware – Help_Help_Help
ransomware. It appears that despite everything it utilizes Nemucod downloader
for spreading around. Notwithstanding, the evildoers have additionally begun
utilizing RIG abuse unit to improve the contamination rates. Be careful with
false messages which can alarm you to survey the connected receipt or archive
all together not to get accused of massive charging.
The present examples of the malware prowl in the doc record
with the installed macros. Fortunately, it isn't hard to look through the
lawful offense. For the most part, the name of the sender does not coordinate
the one given in certifications. Such email would have grammatical error and
sentence structure botches too. The payment notes which are displayed by this
malware are named as _HELP_HELP_HELP_%random%.hta and
_HELP_HELP_HELP_%random%.jpg. The most astounding news is that, in the most
recent forms, its makers chose to quit encoding documents of security programs.
The adaptation which is found by TrendMicro as RANSOM_CERBER.F117AK dodges
firewalls, antivirus programming or antispyware items.
Refresh January 2017: New year have just brought us new
changes in Cerber ransomware. In the wake of making the most recent inquires
about on this malware, specialists found that it turned red. Truth be told, red
shading has appeared in the payoff note of this ransomware that cautions its
casualties about the encryption of their records and a need to pay the payment
in return for the noxious decryptor. Plus, this crypto-infection tends to
utilize .ba99 document expansion which is attached to each casualty's record.
Four arbitrary characters can likewise be annexed.
Luckily, this malware neglects to evacuate Shadow Volume
Copies of these records that it scrambles, what should enable clients to recoup
their information with the assistance of Shadow Explorer and comparative
apparatuses. This form has just been named as Red Cerber, Updated Red Cerber
2017 and Red Cerber 2017. Obviously, subsequent to finding such concerning
news, we foresee that this infection will remain at its pinnacle this year
simply as it did the most recent year.
Have you seen our new blog?
No??
Do have a look: Mercury Retrograde
Likewise, digital hoodlums start the new year with new
Cerber circulation traps. In spite of the fact that they are as yet conveying
enormous heaps of the infection's cases by means of email, now they give off an
impression of being utilizing IP delivers that have a place with Amazon Web Services,
or quickly AWS.
These pernicious messages purportedly contain no headline
and no message, basically a connection. The connection is a ZIP record with a
Word report in it, which contains a Macros content that downloads the
ransomware when the casualty empowers Macros work in Word. Zip chronicles, and
additionally Word archives, are named with an irregular arrangement of digits.
Here are a portion of the pernicious email tends to that lawbreakers are
utilizing to convey Cerber at this moment: vroak[@]otmail.it,
clayton.lively[@]cogentpowerinc.com, kasserer[@]villingevand.dk,
rbrown[@]rsu13.org, and that's just the beginning.
Refresh December 2016: The infection is still effectively
conveyed. As per a report from Microsoft, Cerber ransomware is quickly
multiplying with an assistance of an email spam battle, which conveys secret
key secured .zip documents. Run of the mill email titles contain words like
"Howdy," "Hey" or "Hi," and a short message
soliciting to see substance from the appended document, and giving a secret key
to the connection. Once extricated, records inside this file actuate pernicious
large scale contents that download Donoff Trojan downloader, which downloads
the ransomware to the PC framework.
Read More about : Sporthero Hijacker Removal Guide
Likewise, it is still effectively disseminated through RIG
misuse pack. The casualty just needs to enter a website that has an adventure
pack to enable it to abuse security vulnerabilities in the framework and
download the ransomware without client's assent. The infection has likewise been
seen multiplying its duplicates by means of bargained sites that host Nemucod
infection. These destinations can undoubtedly divert the casualty to Pseudo
Darkleech, which firmly muddles the contamination when Nemucod drops Cerber on
casualty's PC framework.
Discussing the infection's code, we should call attention to
that the Cerber has changed the text style foundation shading from brilliant
green to red. Over that, the most recent form of the infection doesn't touch
Volume Shadow copies, which essentially are a way to information recuperation.
With instruments like ShadowExplorer you can reestablish in any event part of
information scrambled by this ransomware infection!
Refresh November 2016: The crypto-ransomware is currently
assaulting organizations and their PC systems. Strikingly enough,
notwithstanding the Cerber encryption, the infection designers debilitate with
malevolent DDoS assaults that will as far as anyone knows irritate the system
and the general operation of the organization. The programmers start by sending
the organizations a risk email in which they caution about the up and coming
assault and request to pay a set measure of payoff until the given due date.
From that point onward, the aggregate is said to increment. A case of this note
can be seen beneath.
Latest blog update : Astrology
Refresh October 2016: Entering the new month, the geniuses
of this infection don't expect to give the group a chance to take a break as
they presented new threatening highlights. Considering Cerber's present frenzy
in the virtual field, the refresh engages the danger considerably more.
Infection specialists have uncovered that now it adds the
augmentation contained 4 arbitrary numbers and characters. Besides, the
requests are displayed in a .hta record instead of in .html or .txt. Besides,
the infection close down certain database forms in the working framework all
together for the encryption procedure to be finished. Fortunately, these
perceptions may be useful for getting a handle on the operation of the new
form.
Refresh September 2016: There were two unique renditions
exhibited by the proprietors of ransomware infection in September 2016. The
first of them is known as Cerber3 record expansion infection. As you should
have effectively comprehended, it got such name as per the document expansion
attached by it to each of the objective records. This new form of Cerber
ransomware has likewise been thought to be more malignant and dangerous as the
programmers had a lot of time to settle the bugs found in the past two
variants. The second form of this ransomware was found by security analysts
amidst September. As indicated by their report, Ammyy Admin site page was
observed to be infected with the pernicious record used to convey the
crypto-malware.
It was additionally presumed that the site scattered the
infection for a few days, roughly from the thirteenth to fifteenth of
September. The double, which was entitled as an encrypted.exe, was put in
AA_v3.exe. Already, this area was ambushed by other profoundly harming malware
later on. Right now, the site is completely reestablished and alright for open
utilize.
Please take a look on our new article : Kundli
Refresh August 2016: Malware scientists have figured out how
to discover blemishes in ransomware task and figured out how to dispatch a site
that enabled casualties to decode .cerber and .cerber2 petitions for nothing.
In spite of the fact that creators of this site don't give any data on how
could they figure out how to crush the ransomware, some security specialists
had speculated that they have figured out how to discover what the Master
Decryption Key is. It gives the idea this was not valid, and no doubt they have
discovered a defect in infection C&C server. Allegedly, many casualties who
took after news about the infection figured out how to decode their valuable
records for nothing.
Tragically, composed crooks rapidly found the imperfection
and fixed it, so accordingly, it is not any more conceivable to decode records
utilizing this unscrambling administration any longer. In addition, Cerber's
installment site has been enhanced by including Captcha framework, which keeps
away from mechanized endeavors to get to the site. It appears that this pack is
efficient and resolved to keep this infection undefeatable, which is an
appalling actuality. Thusly, PC clients are encouraged to avoid potential risk,
make information reinforcements and ensure PCs with legitimate hostile to
infection answer for forestall ransomware assault, in light of the fact that,
right now, there is no real way to recuperate scrambled information utilizing
unscrambling devices.
No approaches to recuperate records bolted by the scandalous
infection.
According to Wikipedia Checkout the latest news on AntiVirus Software
Shockingly, it is difficult to decode the records bolted by
Cerber ransomware without paying the payoff. Be that as it may, it isn't
prescribed to pay up in light of the fact that:
It just urges the digital offenders to proceed with their
deceitful exercises and make more PC infections;
In addition, remember that there is NO assurance digital
culprits are really going to help you to recoup your documents;
You may not get the decryptor by any stretch of the
imagination, regardless of the possibility that you pay up.
Additionally, this device might be debased, bring other
malware on your PC and along these lines, harm it significantly more.
Latest Article submitted on the topic : Ekadashi 2017
Consequently, you ought not work together with the digital
crooks on any level, on the grounds that their principle goal is to profit, and
they will do their best to attempt their endeavors to pay off.
Erasing the infection from your PC won't dispense with the figure
from the records. Endeavoring to recuperate your documents utilizing programmer
proposed Cerber decryptor device isn't sheltered either. The best choice is to
swing to some more dependable approaches to recoup your information. The
snappiest and the most secure approach to accomplish that is by bringing in
your information from a reinforcement gadget.
We firmly prescribe you NOT to keep the duplicates of your
information on online capacity mists, since some infections can get to them
through your Internet association and degenerate them, as well. It is best to
keep your documents put away on some outer drive and refresh it regularly.
However, there are chances here as well.
On the off chance that the outer drive is connected to the
PC at the season of the infection invasion, the documents in the capacity will
in all likelihood be scrambled as well. Along these lines, ensure that you
unplug the outer stockpiling gadget from your PC each time you reinforcement a
few documents. On the off chance that you don't have a reinforcement, you might
need to attempt these unscrambling apparatuses – Photorec, Kaspersky infection
battling utilities or R-Studio.
Read more on the latest article: How To Remove Internet Speed Tracker Browser Toolbar Virus
Remember that you should take out the Cerber infection from
your gadget totally before you endeavor to recoup your records in both of the
courses specified previously. You can do that utilizing hostile to malware
programming



Now you can order your Kundali or Janamkundli online. Gone are those days when there used to be a need to visit family astrologer for getting your Kundli. Modern technological advancements have made it possible that one can get accurate horoscope at home now as the online astrology softwares now a day facilitate detailed horoscope reports containing with astrology calculations and predictions along with remedies.
ReplyDeleteMywifiext local
ReplyDeleteMywifiext net login
Mywifiext net
Mywifiext
Mywifiext net setup success
Mywifiext login
Mywifiext.net
Mywifiext net setup
www.mywifiext.net
NICE WEBSITE I AM THE BIGGER FAN OF THIS SITE OF your. BUT I WANT TO SHOW YOU THE SOME INFORMATION OF ECLIPSE IN 2019 https://bindassnews.com/lunar-eclipse-2019/ THIS WILL BE THE LUNAR ECLIPSE IN THE YEAR OF 2019 BIGGEST ECLIPSE. So please.
ReplyDeleteThanks for sharing this amazing article.
ReplyDeleteI never heard of Cerber Ransomware before and hope I never have to deal with this. It's unfortunate these situations occur.
ReplyDeletemercurycards.com
www.mercurycards.com
Arlo Support for Arlo Camera Setup Issues, Connection Issues, Multiple Devices Setup, Login Issues etc. Quick Fix for common issues. Call now at 844-456-4180 Toll Free Number for Arlo Support
ReplyDeleteArlo login page secured with 128-bit encryption. Login into Arlo login page to set up newly purchased Arlo camera or you can check easy and quick steps Arlo login troubleshooting.
ReplyDelete<a href="https://my-arlo-login.com/arlo-login-page/>Arlo Login</a>
The information given here is useful to many and the information provided by Virus, Adware, Malware Removal tool is useful to me.
ReplyDeleteonline astrology report
ask astrologer online
talk to astrologer online
Thank You very much it was very helpful and very informative at the same time. Very well effort. Do visit this for getting more help. Thanks for the efforts too.
ReplyDeleteBest Vastu Consultant In Jaipur
Best Vastu Consultant In Jaipur
Best Vastu Consultant In Delhi
Best Vastu Consultant In New Delhi
Best Mahavastu Consultant In Jaipur
Best Mahavastu Consultant In Delhi
Best Mahavastu Consultant In New Delhi
Colourful tapes for vastu
Best shopping site in India
Shopping site in India
Best library management software in India
Best school management software in India
Best interior designer in Jaipur
Best interior designer in Mumbai
Great article with excellent idea i appreciate your post thankyou so much and let keep on sharing your stuffs
ReplyDeletetalk to astrologer
Nice information. For leading website designing and mobile app development company in delhi, visit ogen infosystem for more information.
ReplyDeleteWebsite Designing Company in Delhi
virtualedge Ongoing ‘365 engagement’ is on the horizon, according to event tech providers, but they have yet to form a clear picture of just what it will look like. Community building through virtual events will be key, but how should you fold that into ongoing engagement? out of the office message, virtual fatigue and office team building invitation email sample
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteAuthentic content..very knowledgble.. thanks for this post..
ReplyDeleteTally Financial Accounting
Financial Accounting With Tally
Cerber Ransomware - How To Remove Cerber Ransomware Virus From Your Computer. >>>>> Download Now
ReplyDelete>>>>> Download Full
Cerber Ransomware - How To Remove Cerber Ransomware Virus From Your Computer. >>>>> Download LINK
>>>>> Download Now
Cerber Ransomware - How To Remove Cerber Ransomware Virus From Your Computer. >>>>> Download Full
>>>>> Download LINK 5l
Hi!
ReplyDeleteThis article is written so well and much useful and informative. Thanks for giving such a wonderful informative information. I hope you will publish again such type of post.
Regards
Glitz Life Care
Gluta White
Good Information!
ReplyDeleteMaintenance services Dubai
AC Servicing
Plumbing services near me
Water heater maintenance
Really nice post thanks!
ReplyDeletebathtub repair dubai
Water Heater Repair Dubai
Water Pump Repair in Dubai
Plumbing Services in Dubai
AC Repair Dubai
Plumbing technicians achieve backflow prevention through the creation of an air gap, installation of the Reduced Pressure Backflow Preventer, and barometric loops.
ReplyDeleteProfessional Plumbers Dubai
Water Pump Repair in Dubai
Water Heater Repair Dubai
bathtub repair dubai
Install Security Cam offers Arlo wireless smart home cameras security in USA are backed by 10+ years of experience.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteThanks for this post! If you're looking for a window tinter near Mackay, check here!
ReplyDeleteWe can proudly claim that our team consists of well-trained plumbers. Each has the experience of handling different plumbing issues. You can contact us for any plumbing systems.
ReplyDeleteBathtub repair dubai
Emergency plumber in dubai
water heater repair
Water pump repair